In today’s digital era, businesses and individuals rely heavily on cloud computing to store and access their data. But with convenience comes the crucial question of data security in the cloud. What exactly does it mean, and why is it so important?
Cloud computing refers to the practice of using remote servers hosted on the internet to store, manage, and process data. It offers numerous benefits like scalability, cost-efficiency, and ease of access. However, this convenience also introduces potential risks to the security and privacy of your valuable information.

Data security in the cloud encompasses the measures and protocols implemented to protect your digital assets stored in cloud environments. It involves safeguarding against unauthorized access, data breaches, loss, or corruption. As businesses transition to cloud-based solutions, ensuring the security of sensitive information becomes paramount.
So, why is data security in the cloud crucial for both individuals and businesses? Imagine your data as a treasure chest containing your most valuable possessions. Now picture it stored in a cloud environment. Without proper security measures in place, that chest becomes vulnerable to hackers and cybercriminals who are constantly seeking ways to exploit weaknesses in cloud systems.
Moreover, unauthorized access to your data can lead to severe consequences, including financial loss, reputational damage, and legal implications. Just think about the potential impact of a data breach that compromises your customers’ personal information or your company’s trade secrets. The fallout could be devastating.
In the next sections, we will delve into the intricacies of data security in the cloud. We will explore the risks and challenges associated with it, and provide you with actionable strategies to strengthen your cloud security defenses. Let’s embark on this journey together and ensure that your digital assets remain well-protected in the vast realm of the cloud.
Understanding Data Security in the Cloud
A. Overview of Cloud Storage and its Benefits
Cloud storage has revolutionized the way we store and manage our digital data. It provides numerous advantages that make it an attractive option for businesses and individuals alike. With cloud storage, you can say goodbye to the limitations of physical storage devices and embrace the flexibility of virtual storage.
One of the key benefits of cloud storage is scalability. Whether you need to store a few gigabytes or several terabytes of data, the cloud can effortlessly accommodate your needs. You can easily scale up or down your storage capacity as your requirements change, without the hassle of purchasing and managing physical hardware.
Another advantage is cost-efficiency. Cloud storage eliminates the need for expensive on-premises infrastructure, reducing capital expenditures. Instead, you pay for the storage space you actually use, making it a more cost-effective solution for businesses of all sizes.
Furthermore, cloud storage offers ease of access. Your data is accessible from anywhere with an internet connection, allowing for seamless collaboration and remote work. Whether you’re in the office, at home, or on the go, you can securely access, share, and edit your files with ease.
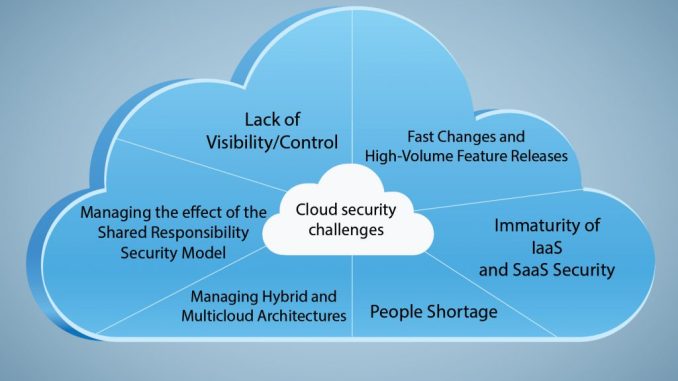
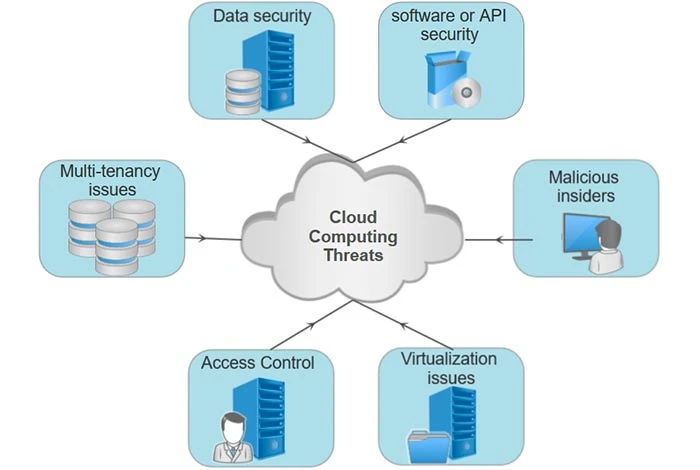
B. Risks and Challenges Associated with Data Security in the Cloud
While cloud storage offers numerous benefits, it also introduces unique risks and challenges to data security. One of the main concerns is data breaches. Cybercriminals are constantly evolving their tactics to exploit vulnerabilities in cloud systems and gain unauthorized access to sensitive information. A single breach can have far-reaching consequences, including financial loss, damage to reputation, and legal implications.
Another challenge is data loss. While cloud service providers implement robust backup and redundancy mechanisms, there is always a possibility of data loss due to technical failures, natural disasters, or human error. It is crucial to have proper backup strategies in place to mitigate the risk of permanent data loss.
C. Common Security Threats and Vulnerabilities
Understanding the common security threats and vulnerabilities in the cloud is essential to protect your data effectively. Some of the prevalent threats include phishing attacks, where cybercriminals attempt to trick users into revealing their login credentials, and malware infections, which can compromise the security of your data and systems.
Additionally, misconfigurations in cloud environments can lead to vulnerabilities. It is essential to ensure that proper access controls and authentication mechanisms are in place to prevent unauthorized access. Regularly updating and patching software, as well as implementing strong encryption protocols, can significantly mitigate the risk of security breaches.
By being aware of these risks and challenges, you are better equipped to implement robust security measures and protect your valuable data in the cloud. In the next section, we will explore best practices that can enhance data security and minimize the vulnerabilities associated with cloud storage.
Best Practices for Data Security in the Cloud
When it comes to data security in the cloud, implementing the right practices is crucial to safeguard your valuable information. Let’s explore some of the best practices that can help fortify your cloud security defenses.
A. Choosing a reputable cloud service provider
Selecting a reputable and trustworthy cloud service provider is the foundation of a robust security framework. Look for providers that have a proven track record in data security and adhere to industry best practices. Consider factors like data encryption, access controls, compliance certifications, and incident response capabilities. Additionally, read customer reviews and evaluate the provider’s reputation in the market.
B. Implementing strong access controls and authentication mechanisms
One of the primary lines of defense against unauthorized access is implementing strong access controls and authentication mechanisms. Utilize multi-factor authentication (MFA) to add an extra layer of security. This ensures that even if one factor is compromised, the attacker still needs additional credentials to gain access. Regularly review and update user access privileges, revoking unnecessary permissions to minimize potential vulnerabilities.
C. Encrypting data at rest and in transit
Encryption acts as a protective shield for your data, making it unreadable to unauthorized individuals. Implement end-to-end encryption to secure data both at rest and in transit. Encryption ensures that even if your data is intercepted, it remains indecipherable. Utilize strong encryption algorithms and ensure encryption keys are securely managed.
D. Regularly backing up data and testing disaster recovery plans
Data loss can occur due to various reasons, including hardware failures, software glitches, or malicious attacks. Regularly back up your data to a separate, secure location to ensure its availability in case of any unforeseen incidents. Additionally, test your disaster recovery plans to ensure they are effective and can quickly restore your systems and data in the event of a disruption.
E. Monitoring and auditing cloud environments
Constant monitoring and auditing of your cloud environments are essential to detect and respond to security incidents promptly. Utilize security monitoring tools to monitor for suspicious activities, anomalous behavior, and potential threats. Regularly review audit logs and conduct vulnerability assessments to identify and address any security gaps or weaknesses.
By implementing these best practices, you can significantly enhance the security of your data in the cloud. Remember, data security is not a one-time endeavor but an ongoing commitment. Stay proactive, stay vigilant, and ensure that your cloud environment remains a fortress protecting your valuable digital assets.
Compliance and Legal Considerations for Cloud Data Security

In the ever-evolving landscape of data security, compliance with relevant regulations and legal considerations is of utmost importance. Let’s explore the key aspects you need to consider when it comes to ensuring data security in the cloud, while maintaining compliance with data protection regulations.
A. Overview of Relevant Data Protection Regulations
Data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), have been enacted to safeguard individuals’ personal information and impose obligations on organizations handling such data. Familiarize yourself with the specific requirements of these regulations to ensure your cloud data security practices align with them.
B. Understanding the Responsibilities of the Cloud Service Provider and the Customer
When it comes to data security in the cloud, it’s crucial to understand the division of responsibilities between the cloud service provider (CSP) and the customer. While CSPs are responsible for the security of the underlying infrastructure, customers are accountable for securing their data and access controls. Familiarize yourself with the specific responsibilities outlined in your service agreements to ensure a comprehensive approach to cloud data security.
C. Ensuring Compliance with Data Security Standards and Certifications
To enhance data security in the cloud and demonstrate your commitment to safeguarding sensitive information, it’s essential to adhere to recognized data security standards and certifications. Standards like ISO/IEC 27001 and SOC 2 provide frameworks to assess and validate the effectiveness of your cloud security controls. Achieving these certifications not only reinforces your credibility but also instills trust in your customers and stakeholders.
By proactively addressing compliance and legal considerations, you establish a solid foundation for data security in the cloud. Stay informed about evolving regulations, understand your responsibilities as a customer or CSP, and aim to meet or exceed industry best practices and certifications. This holistic approach ensures that your cloud data security measures align with legal requirements, providing peace of mind to both your organization and your customers.
Emerging Technologies and Trends in Cloud Data Security

In the ever-evolving landscape of data security in the cloud, emerging technologies and trends play a pivotal role in fortifying your defenses against cyber threats. Let’s explore some of the cutting-edge advancements that can help safeguard your valuable information.
A. Role of Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) have transformed the way organizations combat security breaches. These technologies provide powerful tools for detecting and preventing malicious activities in the cloud. By analyzing vast amounts of data and identifying patterns, AI and ML algorithms can swiftly identify potential threats and respond proactively.
Through anomaly detection, AI and ML algorithms can spot unusual behavior and notify administrators of potential security breaches. This allows for prompt action, minimizing the impact of attacks. Additionally, AI and ML can automate security processes, reducing the burden on human resources and enabling rapid response times.
B. Blockchain Technology for Enhanced Data Integrity and Transparency
Blockchain technology, most commonly associated with cryptocurrencies, offers significant potential in enhancing data integrity and transparency in the cloud. By utilizing a decentralized and immutable ledger, blockchain can provide a secure and tamper-proof environment for storing and verifying data.
In the context of cloud data security, blockchain can ensure the integrity of stored information by creating a transparent and auditable record of every transaction or modification. This technology eliminates the need for a central authority, reducing the risk of data manipulation or unauthorized access.
Additionally, smart contracts based on blockchain can automate and enforce security measures, ensuring compliance with predefined rules. This not only enhances data security but also streamlines processes and reduces the likelihood of human error.
C. Multi-Cloud and Hybrid Cloud Approaches for Increased Data Security
As organizations seek to fortify their cloud data security, multi-cloud and hybrid cloud approaches have gained popularity. These strategies involve distributing data and workloads across multiple cloud service providers or combining private and public cloud infrastructures.
By adopting a multi-cloud or hybrid cloud approach, organizations can mitigate the risk of a single point of failure. If one cloud provider experiences a security breach or downtime, data and services can seamlessly shift to alternative providers or local infrastructure. This redundancy ensures continuity and minimizes the impact of potential disruptions.
Furthermore, multi-cloud and hybrid cloud environments allow organizations to leverage the unique security features and capabilities of different providers. By carefully selecting and integrating various cloud services, organizations can create robust security architectures tailored to their specific needs.
Stay tuned as we continue our exploration of cloud data security in the next section, where we will address compliance and legal considerations that organizations must navigate in their quest for a secure cloud environment.
Conclusion
In conclusion, data security in the cloud is not just a luxury but a necessity in today’s interconnected world. As businesses and individuals increasingly rely on cloud computing to store and manage their data, it is crucial to prioritize the protection of sensitive information.
Throughout this article, we have explored the definition of cloud computing and data security, emphasizing the importance of safeguarding your digital assets in the cloud. We have discussed the risks and challenges associated with cloud data security, including the potential consequences of unauthorized access and data breaches.
To mitigate these risks, we have outlined best practices for data security in the cloud. Choosing a reputable cloud service provider, implementing strong access controls and encryption, regularly backing up data, and monitoring cloud environments are all essential steps to enhance your cloud security posture.
Compliance with relevant data protection regulations and considering emerging technologies like artificial intelligence, machine learning, blockchain, and multi-cloud approaches can further bolster your data security efforts.
We understand the significance of data security in the cloud. We are committed to providing you with the latest insights, strategies, and tools to protect your valuable information. Remember, your data is the lifeblood of your business – guard it with vigilance.
In the vast expanse of the cloud, where your data resides, security must be your guiding star. Let us help you navigate the complexities of data security in the cloud and safeguard your digital assets with utmost care and expertise.
Together, we can ensure that your data remains secure, your business thrives, and your peace of mind remains intact. Stay secure, stay empowered, and embrace the boundless possibilities of the cloud!
